Companies news
Cyber Node’s Insights: What Cyber Threats Mean for Australian SMEs

Despite significant cybersecurity investments, many business leaders see limited ROI; IT teams struggle with complex issues, leaving SMEs vulnerable.
Cyber Node shares insights on cybersecurity for SMEs.
Despite significant investments in cybersecurity, many business leaders today are yet to see their return on investment and effective system defences:
- IT teams often struggle to fully grasp or escalate complex security issues, leaving organizations in the dark.
- In parallel, every business owner is aware of the high-profile cyberattacks that capture public attention—think the Optus or Medibank hacks, overall reinforcing their apprehension. And they are right as, beneath the headlines, countless breaches are quietly occurring every day, especially among small and medium-sized enterprises (SMEs).
Recent data from Webber Insurance’s Data Breaches List reveals that 2024 saw a 20% increase in reported data breaches across Australia. Notably, 60% of these incidents affected businesses with fewer than 100 employees, while medium-sized companies also faced significant threats. In terms of categories, phishing attacks accounted for nearly 45% of breaches, with ransomware responsible for approximately 30%, highlighting the evolving and multifaceted nature of cyber threats.
Consequently, the everyday cyber risks that SMEs face can be devastating, often leading to financial losses, reputational damage, and even liquidation. Therefore, without clear insights into their cybersecurity posture, business leaders are essentially navigating blind, potentially leaving their organizations vulnerable to attack.
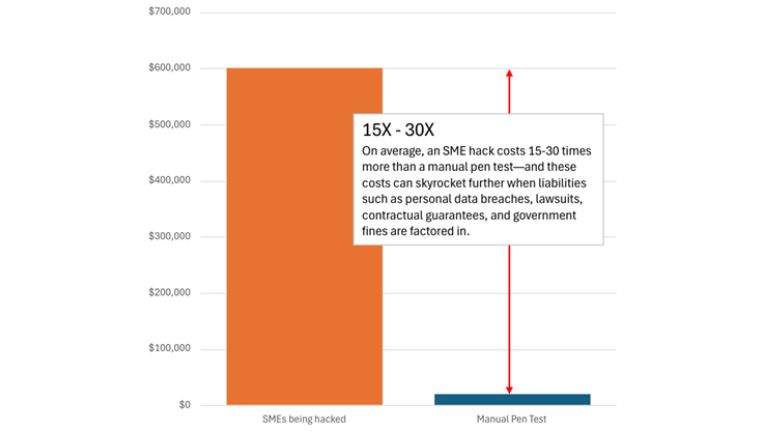
This is where a robust and comprehensive penetration testing process becomes valuable. Advanced manual penetration tests serve as an ultimate stress test for your cybersecurity infrastructure. By meticulously simulating real-world cyberattacks, these tests provide a clear and honest picture of where vulnerabilities lie. Cyber Node’s certified pen testers employ the same tools used by real-world hackers while rigorously adhering to the risk evaluation and reporting guidelines set by NIST, OSCP, and CREST.
Our process starts with a comprehensive Scope Evaluation. Next, we conduct a detailed test phase that typically lasts one to two weeks. After that, your IT team or developers have the opportunity to make necessary fixes, and finally, we perform a Re-Test to confirm that every potential vulnerability has been found and addressed.
By engaging in this thorough testing process, business owners not only gain critical assurance about the strength of their defences but also improve their competitiveness in the market. Enhanced security can lead to reduced insurance premiums and offer an advantage over rivals who may neglect comprehensive cybersecurity measures. In an era where each cyber misstep counts, knowing exactly where you stand is necessary.
Source: Matt Breuillac, Cyber Node


